Tens Of Millions Of Users’ Instagram, Youtube, And More Data Leaked
Surveillance capitalism unilaterally claims human experience as free uncooked material for translation into behavioral knowledge. Although a few of this knowledge is applied to service enhancement, the remaining are declared as a proprietary behavioral surplus, fed into advanced manufacturing processes known as ‘machine intelligence’, and fabricated into prediction merchandise that anticipate what you will do now, soon, and later. Secondly, large databases containing numerous sorts of private information and biometrics can be used to coach algorithms, and automate the demonization of whole communities simply on the idea of how they give the impression of being and even what they put on.
We use net browser and mobile analytics to allow us to understand Network functionality. In doing so, we report information together with, for example how typically you go to the Network, Network efficiency information, errors and debugging information and the kind of activity you interact in whereas on the Network or in your use of our Products and Services. We could on occasion share this data with third events for research or product and companies optimization.
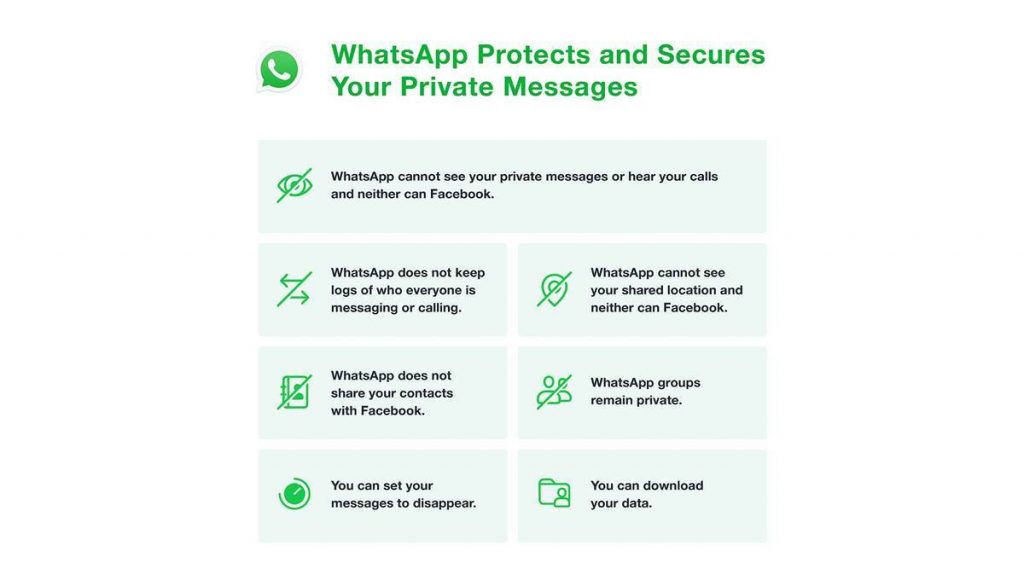
New Safety Flaws In Whatsapp Can Let Cyberattackers Gain Unlawful Access To Customers’ Information
It is understood and agreed by the User/Customer that in no event in any way, the Company shall take any responsibility or legal responsibility for malfunctioning or defect in any cost procedure. This shall be regardless of whether or not the order has been confirmed and/or payment has been levied through a credit card. In the event the cost has been processed by the Company, the same shall be credited to your bank card account within 7-14 working days and duly notified to you by email. Once the order has been placed and in case You wish to cancel/modify the same You may achieve this topic to cancellation/modification costs as prescribed. It is known and agreed by the User/Customer that the Services shall only commence after realization of cash within the accounts of the Company in case the online fee is being opted for by them.
The leak was reported on February 10, post-investigation it was informed to Indane on February sixteen and after no response from the fuel company, the matter was made public on February 19. In no event shall the protected entities be answerable for provision of or failure to offer all or any service by a User/ diagnostic center to any User/ consumer. In no event shall the protected entities be answerable for or in reference to any content posted, transmitted, exchanged, or acquired by or on behalf of any User or other individual on or by way of the Website.
Information Privateness Vs Innovation: The Brand New Guidelines Of The Road
Online marketplaces are an obvious example of the facility of net scraping because nearly all of us use these websites on a regular basis. And while I understand that low-cost flights, discount resort rooms, and rock-bottom gadget costs are most likely not saving the planet, these sites have made many of these services accessible to a wider audience. On prime of that, new aggregator web sites have brought to mild moral producers that produce goods of top of the range underneath honest working conditions. And all of them lack a stronger Data Security strategy that lets these data go away these enterprises’ security infrastructure undetected. The problem right here is the reliance on an older safety approach that’s restricted to the perimeter and lacks knowledge visibility to deal with new-age safety challenges within the given work infrastructure.
IndiaStack, the basic public digital infrastructure behind UPI, has been introduced, to further the target of making financial services accessible to the next billion. The core precept of AA platforms constructed on DEPA is to offer customers full authority over how their knowledge might be used. AAs usually are not permitted to see, inventory, or sell the data ‒ only to gather and transmit it.
Database Admin Engineer
We should also scale up the utilization of digital technology and revolutionary functions. This further involves enhancing tax reforms and bettering debt management capacities, whereas using limited fiscal space to spend cash on priority sectors. Their participation leads to sharing of collective insights on sharing pathways to resilient recovery from health pandemics and financial collapse. In this collection ministers, decision-makers, non-public sectors, and heads of international agencies participate.
1) To address the challenge of diminished fiscal space and debt vulnerability
2) To guarantee sustainable recovery, according to the ambitions of the Paris Agreement and the 2030 Agenda 3) To harness the potential of regional cooperation in help of financing for development.
“Cybercriminals could scrape data from sites for quite a lot of functions, including spamming, info gathering, and social engineering assaults. And once they do ‘comply’ with the law—to reveal how much knowledge they have about you—they present your data however with the vitals lacking or in a type that you can be not comprehended correctly. An NYT report says that the detail by which knowledge is captured is “eye-popping”, like every facet of your kindle e-reader.
The Massive Danger: Facial Recognition
This will involve, on the one hand, repurposing present knowledge troves, and on the opposite, the higher knowledge access and insight gained on account of the new and increased buyer exercise on their platforms. An increasingly popular fintech service right now is API-based banking-as-a-service. This allows third get-together functions to enter data from a bank to provide a service, such as a new banking app enabling wage disbursals from enterprise bank accounts to a quantity of worker bank accounts. Relevant knowledge within the bank’s database is accessed using an application programming interface, that solely offers access to the queried and permitted information. If knowledge science is the field that you are passionate about, you may contemplate pursuing a career in one of these firms or maybe even beginning one.

The mentioned compliance group may appoint or engage any advocate or skilled from inside and/or outdoors the Company to seek their opinion in carrying out their duties as stated underneath this IP Policy. The company shall develop and implement an administration system to help make positive that all personnel observe its IP insurance policies. This management system shall embody all IP-related insurance policies, procedures, and sufficient and correct data essential to implement, measure, and improve Company’s IP protection and compliance program. The Company has adopted this Policy so as to shield its personal IP and reduce the chance of infringement of the Intellectual Property rights of the Company and the Third Parties. This IP Policy goals to provide a clear administrative system for the possession, control, and switch of the IP created and owned by the Company. Third-Party advertising might use third-party promoting firms and/or advert companies to serve advertisements whenever you go to our Website.
What Is Infodemic Management?
The leaked data consists of personal information such as the name, e-mail tackle and phone variety of the users. The fintech service providers are thought-about to be the torchbearers in the financial service business in the post-Covid world. They have the capacity to steer the industry as properly as the financial system to get well from this present crisis.
Through our step, we are sure that there will not be a selected drawback that allowed this information to be scratched in 2019. RMF now requires an additional step, Preparation Step with 18 new Tasks, and the safety management baselines households have increased from 18 to 20 to incorporate extra privacy and provide chain security management households. The President and OMB have additionally elevated the requirement to implement to new CSF course into the FISMA process and DHS has initiated a number of new actions that might be leveraged by enterprises and techniques to extend the safety and meet ongoing authorization efforts. All of those have made major adjustments to Federal Cybersecurity requirements that may have an effect on authorities and contractor information methods and enterprises. This seminar will identify the modifications and supply methods for effectively and shortly implementing solutions for meeting the new necessities. Similar consciousness with data safety norms is also required when creating underlying expertise.
Mysuru: Husband Dies Of Covid
Breach and leaks of the company’s priceless and sensitive data could lead the Companies to be blown down the water with tons of losses. The administration of delicate data ought to be geared up with high-end security and encryption applied sciences with particular and essential rules set for the one making an attempt to enter it. Also, a subject of compliance rules should be set specializing in the servers that can hold and retail the info, guidelines concerning the downloading of copies of information, and sure measures that involve the exposure of the company’s important knowledge.
- Once individuals start to register for the app, the platform will upload bulk data on co-morbidity offered by native authorities.
- We herald a number of security options to offer your essential knowledge the utmost safety and significance.
- Those under quarantine had been checked daily on phone through a call center whilst 14 groups of well-being workers monitored some 4,000 individuals who had entered the district earlier than its sealing.
- Human Rights Watch reveals to us on this interactive website how the system displays all the information accumulating sensors—mobile telephones locations, CCTV images, biometric scanners, to track the movement of people, and ‘suspicious’ behavior can set off alarms for the native police to act.
- The San Diego Union-Tribune reports that Scripps Health, which was hit on May 1st, remains to be in the process of remediation, but hopes to be again to normal operations by the end of this week.
- Further Healthians reserve the proper to refuse Service at any time without offering any causes.
- However, this use of knowledge scraping software might lead to infringing of the intellectual property of an organization or an individual while acquiring knowledge.
In the course of providing you access to the Network, in addition to Products and Services, TPRH collects and receives personal information in a couple of methods. Often, you’ll be able to select what information to offer, but typically we require private information from you to carry out certain actions such as reserving rooms. This section particulars the ways by which we gather info from you and how that data is received. We will want to process your private information in order to give you our Products and Services. By utilizing the Network or purchasing our Products or Services, you affirm that you’ve read and understood this privacy coverage (“Privacy Policy”) together with how and why we use your info and that your use of the Network is topic to the relevant Terms of Service and this Privacy Policy. If you do not want us to collect or course of your personal info as described herein, you could have a number of selections together with limiting the knowledge we collect on you, or not utilizing the Network, or our Products and Services.
Cybersecurity Training Needed For A Secure Work Setting
Building your personal scraping project for extracting the best deals is usually a nice coding project that will speed up your knowledge scientist career. Once you get familiar with the basics of data aggregation you might be able to function open-source scrapers, which can make the work with extra superior scraping bots a walk within the park. Let’s learn more about fundamental information aggregation earlier than progressing to scraping related enterprise alternatives. In some methods, China is setting the standard for a public health response which will turn out to be a lifestyle within the 21st century. Whatever be the case, surveillance and smart public well-being measures might be needed over the next few months.

For more information, please discuss with the consumer assist information in your browser of selection. Please understand that cookies could also be required for certain functionalities, and by blocking these cookies, you could limit your access to certain parts or features of our websites and platforms. We use cookies to compile utilization activity so as to higher cater our offerings to you. We DO NOT share identifiable “raw” knowledge with any third parties, nonetheless, we do make high-level decisions primarily based on aggregated data about your utilization of our Products and Services. We may amend or update this policy once in a while and can notify you of any materials changes to this policy.
Gartner Says Finance Leaders Should Balance Risk Management And Productivity When
The company shall provide acceptable level coaching on IP safety and administration for relevant supply chain members. The company shall present ongoing applicable level coaching on IP safety and administration to all related personnel. The company shall not knowingly purchase or use counterfeit or other infringing items and providers in running its business, including counterfeit trademark items or infringing copyright materials.
One of the basic ways in which businesses perceive their clients is through segmentation. Typically, customers are segmented primarily based on demographics, psychographics, gross sales behavior, and so forth. to focus on them with the best merchandise and offers. At a very large scale — say for an FMCG company like Unilever or retailer like Walmart — performing buyer segmentation manually is increasingly difficult. The streets of many countries are peppered with safety cameras, however, no place else has gone up to now in linking them to huge databases of faces.
Normal Process In India
Furthermore, using the net site might take the consumer to hyperlinks to websites, Application or cell Applications on the Internet that are owned and operated by third parties. User agrees that we are not liable or liable for the content on third get together application. Healthians reserves the best to reschedule or cancel an appointment with none prior notice. The time supplied for session or conducting take a look at is indicative and actual time for availing the Services may change depending on the supply of the phlebotomists. In order to process the funds, Healthians might require details of User’s bank account, bank card number, etc.
What is more likely to change even more dramatically are certainly different aspects relating to political management and security. In this section, a point of social contact with a restricted number of folks may also be allowed, subject to what the situations are then. YASH is a complete and efficient science and health communication effort for promoting grass-roots degree appreciation and response to well-being. They need to aggressively enhance their contact tracing efforts with the assistance of their police who are skilled in debriefing, name report mapping, and have more manpower than public health departments of local administrations. The Union authorities confirmed no inclination towards drafting or enacting COVID-19-specific legislation that could handle all the issues pre-emptively. The Disaster Management Act can’t be applied to pandemics in view of the truth that the power to legislate on public health is vested specifically and exclusively with the States.
Remedies For The Content Material Importer
The User shall be answerable for all makes use of of the User’s account and password, whether or not or not approved by the User. The User shall instantly notify Healthians of any precise or suspected unauthorized use of the User’s account or password. If a User provides any data that is false, inaccurate, not current or incomplete, or Healthians has reasonable grounds to suspect that such data is false, inaccurate, not current, or incomplete, Healthians has the best to suspend or terminate such account at its sole discretion. User does hereby authorize Healthians and its officials to collect the electronic copy of the report from the Diagnostic center/ Labs and provide the identical to the Users. This AA software displays all of the consent offered, rescinded consent, and a document of all data requests made by the FIU.
Moreover, the number of consumer accounts opened by shoppers and the number of searches they had conducted had been also compromised. The firm’s clientele contains major legislation enforcement agencies in the US, together with the FBI and the Department of Homeland Security, and other company companies. The agency is already mired in controversy relating to its use of facial recognition know-how for matching social media images towards suspected criminals’ photographs provided by the police department. Technology is a double-edged sword and the user of such expertise determines the purpose of the identical.
Agile Security
An individual’s or entity’s knowledge is often fragmented and unfolds throughout silos in knowledge warehouses of financial establishments, government bodies, and numerous other enterprise entities. There aren’t any frameworks for seamless, secure, and swift knowledge sharing between financial info providers and monetary information users with the permission of the user whose data is being shared. At the same time, there’s a lack of options and companies to aggregate and combine user data for a seamless, wide-ranging view of knowledge in actual time. Consequently, there’s nonetheless resistance to accessing and sharing of information and an enormous amount of fragmented info isn’t successfully optimized to supply complete service delivery to users. The resolution, many experts feel, ranges from adopting applied sciences ranging from Cloud companies to SD-WAN infrastructure, to raised encryption and increased risk surveillance.

In the scheduled medical part, the shopper needs to choose out a preferred date and time for medicals. Details of those are available on the schedule medical web page and in case of any adjustments, the buyer might be informed accordingly. Review & acceptance – This section contains details of all the knowledge filled up in previous sections for simple evaluation and acceptance of the proposal by the customer. OTP (One-time password) authentication – Customer needs to enter the OTP to authenticate the small print provided within the proposal form. On completion of fee and proposal type filling, a duplicate of the proposal form along with fee acknowledgment might be despatched to the customer’s registered e-mail ID.
#2 Information Science Projects: Ubers Pickup Evaluation
Which will allow China to take advantage of market access across the Association of Southeast Asian Nations, East Asian nations, Australia and New Zealand. There are enough reports of China’s intentions to accumulate financial assets and stakes in banks and companies the world over amid crisis. Europe has shown a willingness to sacrifice private liberties in favor of higher state control. The existing international institutions such as the United Nations, the United Nations Security Council, and theWorld Health Organization are seen to have didn’t measure up to the grave challenge posed by the pandemic.





